Pentester Academy - PACES Certification
After a busy year (2020) of doing the Offensive Security courses, I decided to see what I can take next that would further my penetration testing skillset. Most of what I found was in line with what I’ve already done until I came across the PACES certification from Pentester Academy.
To obtain the PACES certification, you need to go through their “Global Central Bank Cyber Range Lab”. The details for the course are available at https://www.pentesteracademy.com/gcb.
The image below shows the lab layout, as obtained from their website.
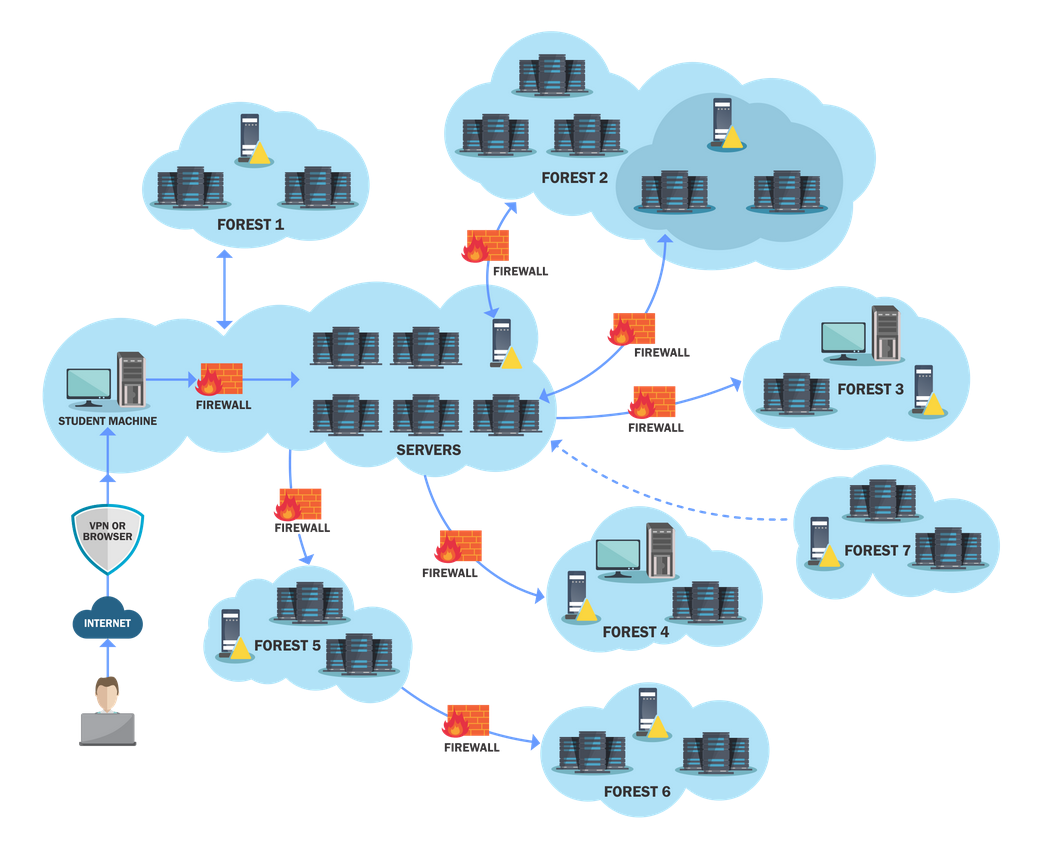
The key learnings boast a list of 46 challenges that need to be completed in an estimated time of 450 hours. I was intrigued, and lucky for me, my employer was more than willing to pay for me to take this course.
I signed up and got access on 3 February 2022.
I’ll write about my time during the lab and my experience in the exam here. This document will be a work in progress.
Updates to this post
2022-02-11: Course introduction and Week 1
2022-02-18: Week 2
2022-02-28: Week 3
Week 1
Course material
I started watching the videos and accompanying slides that are provided as the course material. The material goes into the following topics:
- PAM Trusts
- Local Administrator Password Solution (LAPS)
- PowerShell Web Access (PSWA)
- Windows Subsystem for Linux (WSL)
- PrinterBug
- Resource-Based Constrained Delegation (RBCD)
- Just Enough Administration (JEA)
- Exchange Groups
The only topics that I haven’t come across yet were PAM Trusts, JEA, and the Exchange Groups abuse.
It was during watching the first video that I already hit my first snag in the lab. I loaded up the student VM to run the commands in the video to see how it works. I noticed that I am logged in as a low privilege user on the VM, which means I cannot install any tools, and any tools (PowerView) I am uploading that are deemed malicious by Windows Defender are blocked.
Abandon the path
I find that it’s not possible, at this stage, to follow along with the course notes. You need your separate lab environment setup so that you can follow along with the commands. At this stage, I am still worried that I would not have enough time to complete the lab, so I decided to abandon going through the course notes for now and start on the labs. I figured that I will most likely come across sections where I would have to use the knowledge from each of these topics somewhere in the lab, so I will tackle that when I get there.
The lab
I struggle for about half a day to get anywhere meaningful in the lab. Most of the time is spent trying to figure out what tools I can use that will allow me to start enumeration. The lab environment is huge, so I think initially I am just overwhelmed. There is also not much instruction on what we’re supposed to be doing, or so I thought at least.
Learning something new
This led me to my first discovery. The AD module for Powershell is not installed on the VM, and I couldn’t install it myself because you need administrator privileges. After a bit of research, I found out that I can simply upload my own Microsoft.ActiveDirectory.Management.dll and import it manually into Powershell.
The command you would use to load it:
Import-Module .\Microsoft.ActiveDirectory.Management.dll
This at least allowed me to start enumeration using the standard AD module that is not blocked by Windows Defender.
Eventually, I find a way to compromise my first server, thanks to Bloodhound. Now, I’ve read a few reviews of people doing the GCB lab, and so far they have all said they used their student VM to perform all attacks. I’m a Linux user, so I prefer being able to run the tools I am used to and use daily in my job. I normally use tools like crackmapexec, impacket, etc. To be able to do this though, I need to set up dynamic port forwarding and pivot into the network. This would allow me to run the commands from my own Kali attack machine.
First attempt at pivoting
That’s easy enough right? I just drop chisel onto the student VM, fire it up to connect back to me, and then use proxychains to tunnel all my traffic through the connection. It would be easy if chisel isn’t picked up by Windows Defender as malicious. That brings me back to the fact that I only have low privileges on my student VM.
I spend countless further hours figuring out what I can use for port forwarding. I can find options to use that allow for forwarding one port at a time, but based on the size of the lab, I thought it wouldn’t be an option. I decided to keep spending time on getting this initial proxying sorted, otherwise, I would be struggling for the duration of the lab.
I have previously developed a Powershell payload that would allow me to have a meterpreter reverse shell without Windows Defender detecting it. I decide to modify it a bit and try it in this lab too. It worked, and I got a meterpreter shell. I just couldn’t get the pivoting to work through this connection though, even though I’ve done it a 100 if not 1000 times before.
Support
I read and reread the email I got as part of my welcoming kit, and I finally break down and decide to email the support team. At this stage, I’m pretty sure I’m either missing a crucial piece of information, or the first step of this lab is that you have to perform some privilege escalation on your own student VM.
I have done several certifications, and I have developed a try harder attitude regarding any studying. I don’t have any issue struggling for days trying to find an answer to something before asking for a hint or a nudge from someone. It’s not that I don’t value the help I can get from someone else and I don’t overlook the fact that I could save a lot of time by just asking. I find that this struggle has often led me to learn other things, and once I have figured it out, I would understand exactly where my initial shortcomings were.
The stress of having limited time for the lab got to me though, and I decided that it would save time. While I waited for a response, I did enumeration on the student VM, but couldn’t find any type of privilege escalation. There is stuff that I noticed, but without giving too much away, I just never thought that this would be the route because of the course description.
I receive feedback from the support team, indicating that the privilege escalation on the student VM is indeed the first step in the lab.
Everything clicks for me, and I can use the finding (that I didn’t think would be applicable), to escalate to become an administrator user on my own student VM.
Let’s go
With enough privileges on my own student VM, I could sort out pivoting. This set me up for continuing through the lab.
I make quite good progress, and the majority of the stuff I have to go through are things I’ve learned and used previously, but just with some small twists. For example, if I was used to using a technique on a user account, the path in the lab would require me to perform that technique on a computer account.
Speaking to another student, it seems that having done CRTO and CRTE would help you during this course.
Techniques / skills / attacks
What I’ve needed to make use of during this week:
- LAPS
- WSL
- Stored tickets
- Stored credentials
- LSASS
- Kerberoasting
- PSWA
- Pivoting and double pivoting (and lots of it)
- RBCD
- Constrained delegation
- Domain trust abuse
Progress
During this first week, I was able to complete sections 1 to 6.
Week 2
This week has gone a little bit easier. There was a frustrating part that I had to reach out to the lab team to reset one particular box several times.
It is a box where you have to abuse JEA, and although after quite a bit of fiddling around to figure out how to abuse it, every time I performed the commands, the service would crash and I could not access the box again.
Even after confirming with the lab team that what I am doing is right, it still kept crashing for me. The lab team is awesome and very helpful. They even performed the commands on the VM for me and left the windows open so that I could see what they were doing to perform the attack. I would then ask them to reset the box again, perform the same commands, but it would crash for me. I decided to go onto other sections, to give this one a bit of a break. Eventually, I came back to this, and saw the reason mine wasn’t working, was due to the way I was passing my credentials to the commands.
I’ve been taking the time this week to learn how to use the student VM (Windows) a lot more to do my enumeration and attacks. This makes the process a lot faster than having to set up pivoting for each machine every time.
SimpleHTTPServer.ps1
It’s also during this week that I created SimpleHTTPServer.ps1. This helped me to not have to serve files directly from my student VM.
Pivoting and copying files
I also manage to find something interesting in terms of pivoting and copying files through to unreachable hosts. I wrote about it here Powershell Pivoting.
Techniques / skills / attacks
What I’ve needed to make use of during this week:
- JEA
- Unconstrained delegation
- Post exploitation enumeration
- Anti Virus evasion
- Kerberos ticket abuse
- Active Directory ACL abuse
- WSUS abuse
- Hyper-V Virtual Machines
Progress
During this week, I was able to complete sections 8 to 12.
Week 3
This was a bit of a frustrating week. One of the techniques that needed to be used in the last section, 7, was phishing. The idea is to phish one of the users in the lab, to get a reverse shell to their workstation. I tried various payloads from previous learnings, i.e. Word docs, excel docs, executable files, batch files, linked in the email, etc.
I eventually had to reach out for a hint. There is a very specific way to obtain the reverse shell here, and I’m still not sure how I would’ve ever worked out the right combination by myself.
But once I got the hint, it still wasn’t plain sailing from there, unfortunately. It seems like the automated script that simulates the user being compromised by the phishing attack, dies unexpectedly now and then. I had to ask to have the box reset several times while trying to finish off this section.
From there I was able to complete section 7, which also meant that I was done with the lab.
The next goal was to use the remaining time to go through the labs again, more thoroughly, and make sure I have my enumeration skills down for the exam. At the same time, I’m going to be researching what are the remediation steps that are needed to fix the misconfigurations that I exploit during the lab.
Techniques / skills / attacks
What I’ve needed to make use of during this week:
- Phishing attacks
- Microsoft Exchange groups abuses
Progress
During this week, I was able to complete section 7.
Week 4
I decided to take a little bit of a break from the labs, and at the same time, it got a bit busier at work. I spent a little bit of time this week trying to get my Powershell Active Directory enumeration skills honed in a bit more.
Week 5
I’ve done my final run-through of the labs, and have set my exam for 29 March 2022.
