OSCE3 - Started from the bottom.... now I'm here
After a long year of studying, and lots of hard work, I finally received the email confirming that I had passed my last exam and obtained my OSCE3 certification on 13 November 2021.
To know a bit more about what OSCE3 is, here is an extract from Offensive Security. I’ll also discuss each of the courses further along.
Offensive Security Certified Expert 3 (OSCE3) holders have expert-level penetration testing skills. They have proven that they can craft their own exploits, review advanced source code in web apps to identify vulnerabilities, and have the skills & expertise necessary to conduct penetration tests against hardened systems. By passing the exams a student is automatically granted their OSCE3, demonstrating expertise in 3 primary learning paths: PenTesting, Web Application Attacks, and Exploit Dev.
OSCE3 holders must have passed all three of Offensive Security’s 300-level courses: Windows User Mode Exploit Development (EXP-301), Evasion Techniques and Breaching Defenses (PEN-300), and Advanced Web Attacks and Exploitation (WEB-300).
OSCP
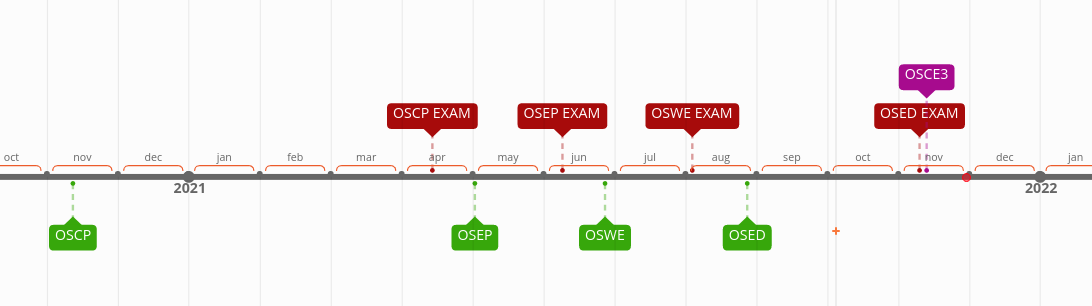
On 15 November 2020, at 02:00 AM, my lab time for OSCP started.
The exam was on 14 April 2021, starting at 12:00 PM.
Soon after getting my notification that I passed my OSCP exam, I saw that Offensive Security was running a special. There was a significant discount if you signed up and paid for OSEP, OSWE and OSED together. I bit the bullet, maxed out credit cards, and signed up for the special. I’m glad I did, because shortly after that, they stopped offering this package deal.
OSEP
On 2 May 2021, at 02:00 AM, my lab time for OSEP started.
The exam was on 9 June 2021, starting at 13:00 PM.
Fresh out of OSCP, I decided that OSEP would probably be the one that will follow on the best. Reading through the syllabis, I noticed predominantly Active Directory and Anti-Virus Evasion topics. Active Directory (and Windows in general) had been a weak point for me, so nothing like forcing myself and being thrown into the deep end to see if I can swim.
A wrote a seperate article about OSEP here.
OSWE
On 27 June 2021, at 02:00 AM, my lab time for OSWE started.
The exam was on 4 August 2021, starting at 03:00 AM.
This course was the one where I was more familiar with the content. It helped me improve on my web application attack skills.
A wrote a seperate article about OSWE here.
OSED
On 28 August 2021, at 07:00 AM, my lab time for OSED started.
The exam was on 10 November 2021, starting at 20:00 PM.
I always knew this one was going to be the toughest course out of the lot. In prepration for this course, I did a x86 assembly course, just to get familiar again with assembly.
For OSED I really had to “try harder” from about 15% into the course content. I learned a lot, and I had tons of fun with this course. As difficult as it was to grasp some concepts, Offensive Security really has a way of explaining things in a way that you can grasp it. As with all their courses, this one started right from the beginning with baby steps, and steadily progressed into advanced topics.
I will still, eventually, take time to write a separate post about my experience with OSED.
Timeline